51 | Add to Reading ListSource URL: math.colorado.eduLanguage: English - Date: 2015-10-18 16:52:38
|
|---|
52 | Add to Reading ListSource URL: web.cs.ucdavis.eduLanguage: English - Date: 2012-05-16 03:26:41
|
|---|
53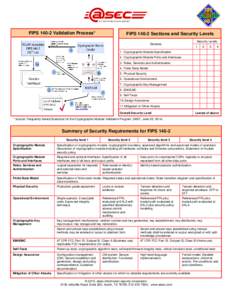 | Add to Reading ListSource URL: www.atsec.comLanguage: English - Date: 2015-12-09 15:15:24
|
|---|
54 | Add to Reading ListSource URL: www.enovatech.netLanguage: English - Date: 2013-01-11 00:43:12
|
|---|
55 | Add to Reading ListSource URL: csrc.nist.govLanguage: English - Date: 2016-06-02 15:30:24
|
|---|
56 | Add to Reading ListSource URL: csrc.nist.govLanguage: English - Date: 2016-07-08 11:48:52
|
|---|
57 | Add to Reading ListSource URL: legacy.python.orgLanguage: English - Date: 2006-05-04 17:09:08
|
|---|
58 | Add to Reading ListSource URL: eprint.iacr.orgLanguage: English - Date: 2015-09-10 11:24:57
|
|---|
59 | Add to Reading ListSource URL: eprint.iacr.orgLanguage: English - Date: 2016-06-01 09:51:10
|
|---|
60 | Add to Reading ListSource URL: www.fkerschbaum.orgLanguage: English - Date: 2013-03-24 11:27:34
|
|---|